Update 2023.10.20: there is a newer version on Github [3] I'm running ClamAV [1] on an Ubuntu 18.04 server in Docker and wanted to document, for posteriority and my own dementia, the setup process and considerations. Thankfully there is an official (?), well-maintained ClamAV image on Docker hub. ClamAV can run stand-alone or as a … Continue reading Running clamav in Docker under Linux
Category: security
Building the perfect, cheap DIY NAS
This post was extensively discussed on Hacker News.Alex Buznik, nas.net.ua kindly provided a two-part Russian translation: part1 and part2. This post discusses hardware considerations, installing Linux, setting up software RAID, robustness and dealing with data corruption. I've been running for a decade a self-built NAS at home, so I thought I'd write down my experience … Continue reading Building the perfect, cheap DIY NAS
Azure diaries: can’t access KeyVault
Context: as a tenant administrator you can't inspect KeyVault contents created by other people ("you are unauthorized to view these contents"). Solution: assign yourself appropriate permissions like this: Locate the KeyVault in the Azure portal: go to "Access policies"click "+Add Access Policy"Key permissions: everything under "Key Management Operations" and "Cryptographic Operations"Accordingly for key and certificate … Continue reading Azure diaries: can’t access KeyVault
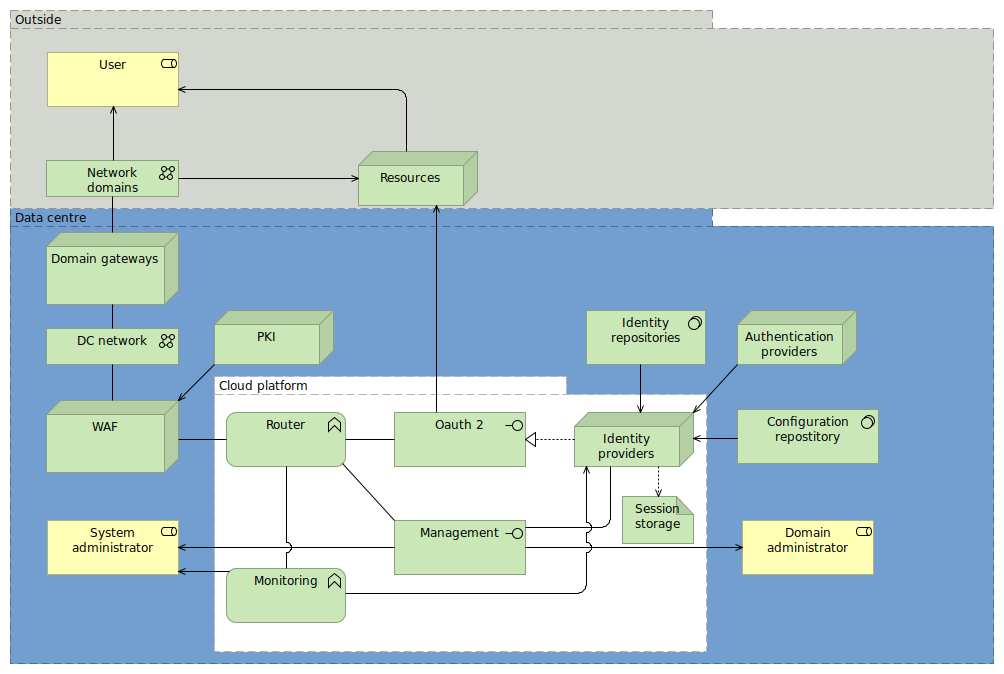
Case study: scalable, extensible identity provider
Slides for a scalable, robust OIDC identity provider with an extensible architecture.
A comprehensive security enterprise architecture
I obtained permission to publish my presentation for an internal gig of a security enterprise architecture. When setting up a security architecture in the enterprise context topics like business continuity, people and processes, governance, services and technology are relevant. https://www.slideshare.net/GeorgeGeorgovassilis/security-architecture-127061728